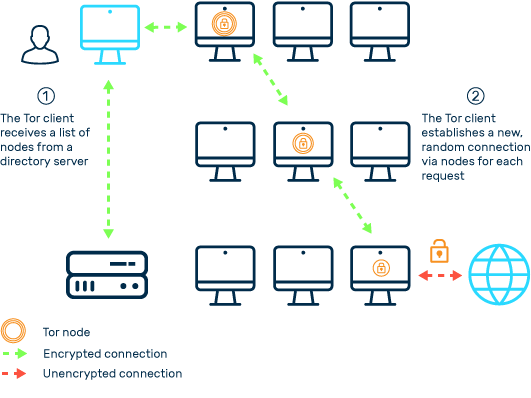
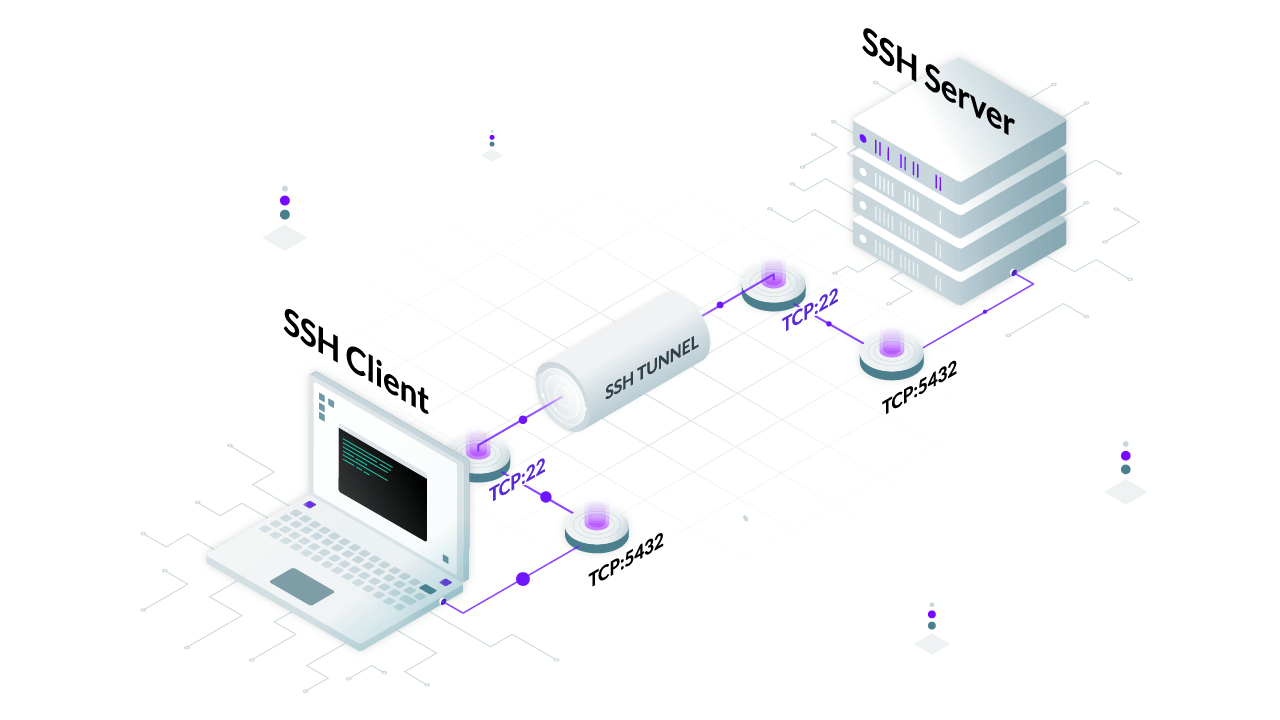
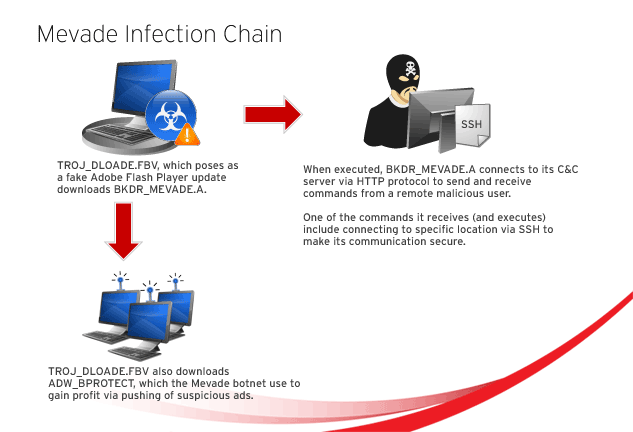
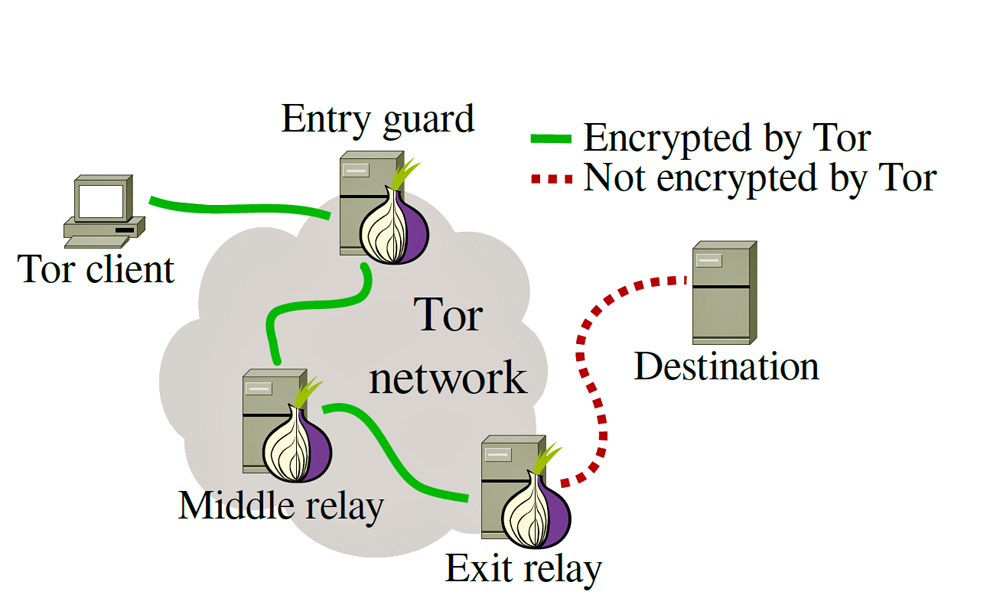
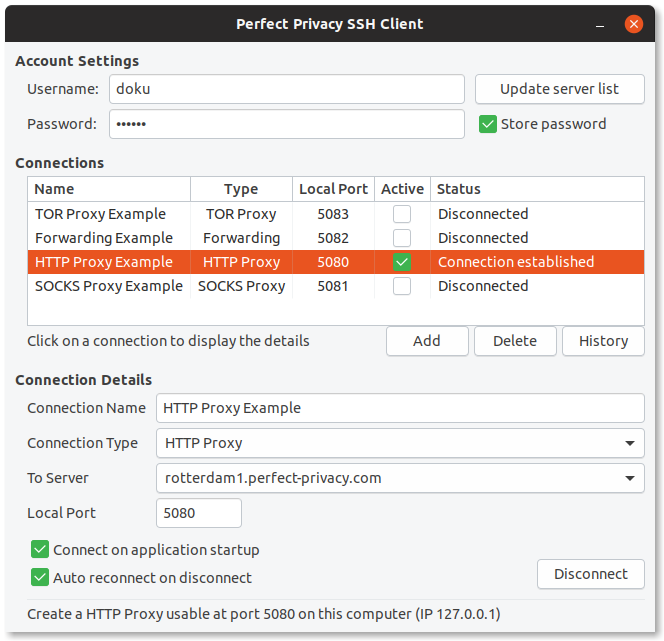
ROC curves of detecting SSH connections through Tor on two different... | Download Scientific Diagram

torcrack - a Tor-enabled threaded SSH brute force dictionary attack written in Python3 (since you guys seemed to like my last script, I thought I'd share more) : r/HowToHack